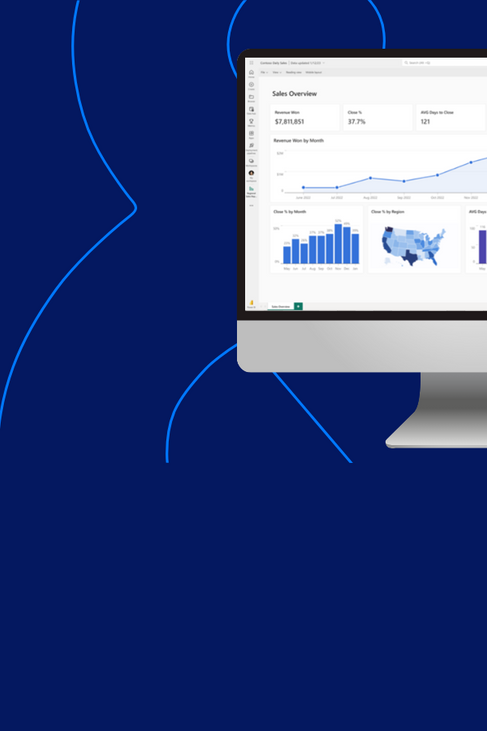
Complete Consulting & Financial Services
SC&H is driving business, technology, and teams forward. From strategic advice that propels growth to insightful data that shapes your future, we’re humanizing the interactions that matter most to you.
Services
Your plans are our priority. From strategy and implementation to continuous support, we bring personalized expertise and practical solutions to meet your objectives while educating and empowering your people. With every engagement, you can count on a qualified team that genuinely cares and delivers results at every stage of your business lifecycle.
OVERVIEWAdvisory & Transformation
Accelerate digital and financial transformation for strategic growth. From actionable roadmaps to innovative technology and data solutions, we provide guidance to help your business scale and thrive.
LEARN MORETechnology
Rapid business growth can strain your technology. Enhance your digital infrastructure, streamline operations, and drive efficiency with the right solutions now and a future-looking plan to benefit your people, customers, and bottom line.
LEARN MORERisk
Proactively manage financial, operational, and regulatory risks to protect your reputation. We help safeguard your business by identifying, assessing, and mitigating potential threats, ensuring resilience in the face of adversity.
LEARN MOREAccounting
Leave your financial management and HR administration to us. We simplify back-end processes, ensuring accuracy, compliance, and efficiency. From bookkeeping to financial reporting, we transform your core financials to drive strategic growth and profitability.
LEARN MORETax
Maximize tax advantages and reduce liability with strategic, integrated tax solutions tailored to your evolving needs. Our seasoned advisors offer personalized, year-round compliance, drawing on over 30 years of award-winning expertise.
LEARN MOREAudit
Gain the highest level of financial assurance with comprehensive, compliant audits that build trust with your shareholders and consumers. We reliably fulfill your reporting needs, offering industry expertise for long-term organizational value.
LEARN MORECapital
Investment banking with a personal touch. We help you navigate complex financial transactions and maximize business value throughout your lifecycle, providing informed guidance for long-term success.
LEARN MOREWealth
Grow your wealth and achieve meaningful lifestyle milestones. Serving as your fiduciary partner, our advisors, CFPs, and CPAs offer integrated financial plans and strategic tax advice for future-focused individuals and families.
LEARN MOREYour Success Matters Here
You can’t afford to fail, neither can we. So, we listen intently and align our solutions with what you need, not what’s convenient. From big plans and high expectations to small budgets and low buy-in, we understand your challenges. Our goal is to create momentum that leads to results and empowers your team. You’ve got this, we’re just here to accelerate things.
About Us
Since 1991, we’ve ditched transactional engagements for rewarding experiences that meet the needs of the middle-market, Fortune 500s, SMBs, and high-net-worth individuals we serve.
LEARN MORECareers
SC&H is a place that champions your success. Every day here is an opportunity to advance your career and achieve rewarding milestones alongside people who care about your growth.
JOIN THE TEAMA Career at SC&H Creates a Lifetime of Opportunities
From career trajectory and an inclusive culture to professional development and serving clients, learn what makes our workplace unique.
The One-Stop Shop Powering Your Full Potential
Feeling overwhelmed by financial complexities and strategic roadblocks? We get it. Our end-to-end consulting and financial services are designed to work seamlessly together, getting you to your goals faster and more efficiently. Stay in lockstep with the pace of change with SC&H.
EXPLORE OUR SUITE OF SERVICES
Core Technologies
We empower your innovation through strategic technology alliances with leading providers. Our partnerships enable us to help your team transform faster and achieve lasting results.